Away from Centralized Services
A personal tale of moving away from centralized services
November 2018
Why this talk ... Getting in touch with the developers and a wider community of open, decentralized blockchain platforms would require us to use closed, centralized communication channels. What we end up with, is having logos of such communications companies littering the websites that are promoting the very opposite values. In a bizarre turn of events, we use the names of these companies even as verbs, thus sublimely advertising their platforms, engraving their names into our subconsciousness. This happens whenever blockchain projects invite users to join their community by “whatsapping them” or inviting them to click on the logos (that is, advertisements) to engage communication, a grotesque indication of modern times. In a chilling experience, I was witnessing a core developers meetup of Ethereum Swarm, with their presentation delivered from - Google Docs. Here, I propose that open projects, such as those on the image bellow, please use more neutral ways and take steps in migrating to open communication rails, better aligned with their vision.
Centralized Services
We are surrounded with centralized services and centralized ledgers. I have enrolled in the pioneering MOOC about digital currencies by the University of Nicosia back in 2013. We started our journey with the careful observation of how these centralized ledgers are recording our lives without us making abig deal out of it. Centralized services are not a priori evil – usually they operate quite perfectly and are comparatively very efficient. However, relying on them 100%, be it with hardware (think of the chip in your phone), software or wetware (humans), sooner or later ends up with censorship, corruption, unavailability. We want to minimize the risks that come from relying on them too much. Since I’ve become a teaching fellow at UNIC (see https://digitalcurrency.unic.ac.cy/about-the-program/curriculum/, course Blockchain Technology and Applications and course Digital Currency Programming), I always start all my courses with this consideration, paving the necessary mindset to appreciate de-centralized products and services.
Digital life ...
Contemplating about my own digital life, I’ve summed it up into three activities, which are all operating on a certain infrastructural setting. My goal is to make a safer environment for my digital self.
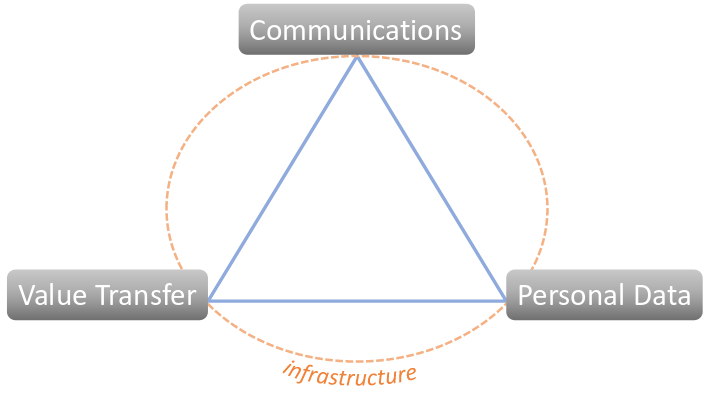
Communications plays an ever more important part and is in many ways an encompassing activity to all others. A variety of challenges are facing us with regards to: reasonably friendly communication media, security of message transport, quality of service. A pesky little itch with communication is defining the line between a phone and a computer.
Transferring value gets discussed in great lengths, yet we often prefer to neglect any inconveniences that await us. How do we store the private keys, protecting our digital money? Ah, keys. Where do you store the keys of your lambo? Not trivial questions.
Managing our data is fuzzy, we rather not spend too much time thinking about it. We like keeping our personal data on local devices, but just the pain of plugging the cables is detrimental to the user experience. Having an adequate backup process most often isn’t appreciated until the very catastrophe happens. For the sake of relieving these pains, storing personal data "in the cloud" has already become the norm. Here, I challenge the notion of a cloud to that being "on someone else’s computer".
Supporting all these activities is the underlying infrastructure, the environment that digital selves live in. An example of such an infrastructure would be a physical layer such as a personal computer and the first layer of software that is an operating system. Here, more inconvenience awaits: separating offline operations from online, drawing the line between various digital personas we use to partition our digital presence to different IT services, segregating the activities that require higher security levels from acceptably untrusted ones, etc.
Have you ever asked yourself how many computers are inside any of your devices? (see https://www.gwern.net/Turing-complete#how-many-computers-are-in-your-computer) There are enough layers and black boxes that one was to desolately give up any hope for security (which is liberty) - that is, if it would be practically feasible. Worst case come true, we are in it already way too deep, but just by observing all kinds of technical failures in our daily lives, it is reasonable to expect that exploiting any complex computing system is prone to the same bug-ridden code, faulty manufacturing and political non-determinism, making it vulnerable to exploitable loopholes inside exploitable loopholes. Abusing the malware, hacking the hackers, spying on spies. Finally, it is about buying enough time to do our thing in peace before getting cut off (see Cory Doctorow's talk at DevCon 4, https://youtu.be/JE4yoU6ssi8), for which there needs to be an opportunity at the very least. Hence, it is about giving the edges a credible chance.
Value Transfer ... our "crypto needs"
What could be done to improve the delicate practice of transferring value in the digital world? Tricky challenge, because a single mistake in any of the steps involved ends up with a catastrophe, not unlike losing paper cash from your pocket which the first bywalker would pick up and that would be the end of it.
>> “Not your keys, not your coins.” << This notorious axiom is multi-layered. If you’re not really controlling your private keys, someone else is very interested in doing that for you. However, there is more to this. Run your own node? Not enough. Use your own node!
By running our own nodes, we indeed verify all transactions on our own, but if we are using then a closed-source wallet on an opaque device that connects to an unknown node, we are introducing a phantom – we would like to avoid that. Use a trusted node, preferably your own. There are some wallets enabling you to use a “trusted peer”, for example Bitcoin Wallet on Android.
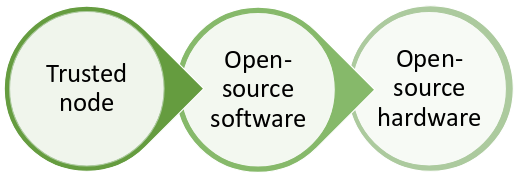
Use open-source products, esp. in the blockchain space. Blockchain is about sovereignty, it is about participants being equal peers, it is about not trusting anyone and verifying everything. With open source software, the user knows what the software is doing. How? User can inspect the source code and compile directly - or,more likely, he/she can at least verify the provenance of the downloaded software by checking that the release is signed with the signing key of the software maintainer (check that the release is signed with the PGP key that you trust – obtain that key of the signer from a source that you trust, maybe you’ve met the signer in person and he/she gave you her public key, yes, people do that, then download the signature and verify it against the downloaded release).
A step further is open hardware, which is not as widespread, but there are several shy options still. For example, instead of using a password manager "in the cloud", we can use an open hardware device such as Mooltipass, featuring state-of-the-art security, with unscratched openness and usability. Then there are open protocols for second-factor authentication, that should replace 2FA relying on closed-source third-party shenanigans, and are extremely versatile, like FIDO U2F standard. Universal 2nd Factor is an open, strong authentication standard, managed by Fast IDentity Online consortium of several major tech players. See: https://fidoalliance.org/download/
Operating system ...
Everything that I do for work is via a computer. When my old working horse died, after serving many years, I bought a new, top shelf model, which must now endure for a long and hard-working usage. Unfortunately, the joy of playing with a new tool immediately got bitter. There was no option to buy this computer without embedded Microsoft Windows 10 operating system. A dangerous marketing tactic. Deciding to give it a try at least, I proceeded with the installation. To my surprise, the computer talked to me through some kind of a "voice assistant", which tried to be semi-humanized by giving it a name, Cortana, and it requested me to register online – just like that, not much description why I need to register and what benefits are there for me by doing so, the installation would just not continue if I don't comply. In my opinion, such tricks are over the top by a significant margin. This practice is wrong on so many levels, that I was given no choice whatsoever but to format the pre-defined disk partition and started looking for a saner operating system.
An operating system that I don’t know what it is doing, is a loophole I don’t need. Having it connect to some unknown online services, sharing whatever data it deems "necessary to improve my user experience" (a.k.a. spying), is simply over the top.
Reasonably secure Qubes OS
Thus, I’ve chosen a "reasonably secure" Qubes OS. It ticked the most boxes for me and I am enjoying it for almost a year now. Qubes is open-source, naturally, made by the pioneering work of Joanna Rutkowska, one of the most respectful security experts, with very low-level experience in exposing operating systems vulnerabilities (see her work on The Blue Pill, https://en.wikipedia.org/wiki/Blue_Pill_%28software%29). The way Qubes OS achieves extremely high levels of security is by virtual separation of user’s activities, they call it compartmentalization. Think of a set of drawers, each containing things that go together. An array of virtual machines, called qubes. With a cherry on top - friendly management.
When you first start using Qubes OS, you have to think about the things that you do on a computer, what kind of devices you require and for what purposes, how are different activities connected and so on. It might take several iterations. This is how my system looks in essence, though there are more complexities underneath. It looks like a headache, but is very straightforward and works seamlessly.
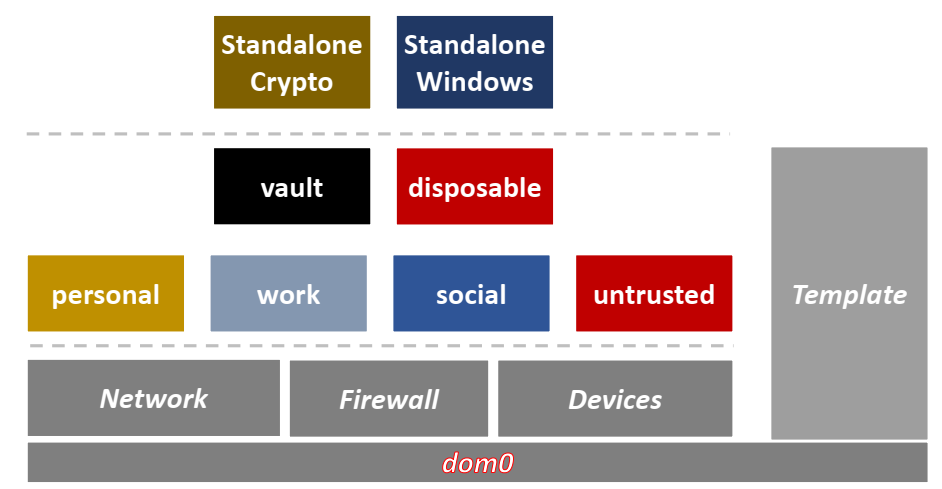
I have a personal compartment, which is where I access my private emails, do personal video conferencing, interact with my bank, keep personal data etc. Then I have a separate virtual machine where I do all my work, it has lots of installed software that is unstable and potentially dangerous, so I don’t want it to affect my personal digital life. There is then a special compartment which I use strictly for “social media” [sic!] platforms. I’ve decided to put all these googles, linkedins, reddits, twitters and such in the same box, let them spy on each other if they want, but they will have none of my personal or work life. All the regular internet browsing I do in an untrusted virtual machine. It has no access to external devices, gets cleaned often, and I generally consider it as already compromised. There is a disposable virtual machine, too, which is a sandbox. I use it to install software that I just need to check briefly, or maybe access a dangerous website or just test something quickly. This disposable VM gets discarded as soon as you click on X. If you mess it up, just close it and your computer stays unaffected. A new, clean sandbox is always just a click away, fantastic. Lastly, as a final normal compartment, there is vault. This one is very small and has no access to the network at all. This is the offline part of my otherwise always online computer. This is where I keep a password manager. If any of other compartments gets compromised (or just crashes), it will have no effect on vault. No other VM can access it, no device can access it, it is, well, a vault. Whenever I need to copy the password from vault and paste it in other VM, there is a special copy-paste procedure, meaning that interactions between each qube needs your specific permission every time. Sounds convoluted, but actually it is just a press of a button and does not cause any friction to the UX.
An additional feature of Qubes is that the devices, like microphones and external disks, have customized access to particular qubes. No need to worry that a webcam will spy on you. It can not. If I am to make a video call in my personal qube, I assign the microphone and the webcam to that particular qube specifically. I do my call and detach the device afterwards. Can the webcam still spy on me? Ah, no go. There is (at least) one VM that is specifying the access to your networks, the firewall rules are defined in the other VM, the devices are separate qubes etc. Nothing can slip through as the access is defined at the lowest level. A side effect is that no qube can access the whole screen (!), it would actually be interpreted as a security breach. Each qube in Qubes OS has its own color of the title bar, making you distinguish between different qubes very easily. A more nagging side effect is that screen sharing is prohibited, yes, truly. In Qubes perspective, you simply cannot have one application having a complete access over your screen. This alone is worth spending a couple of moments, because it is a harsh measure, however the insight of understanding the implications is quite profound.
Managing so many virtual machines could be a nightmare, except that it isn’t. Most of these VMs are managed via templates. Whenever there are updates or you have a need to install some software, you do it in a template and changes will be picked up by corresponding qubes. Thus, a qube can be thought of as just an implementation of the template with its own data and rules.
There can be standalone qubes as well, not based on any template. I use one for some particular activities within the realm of cryptocurrencies. And I do have a Windows standalone VM, for the sake of supporting some of my clients and for the admittedly superior Microsoft Office suite.
Keeping all these virtual machines in order, there is an overarching dom0. It is a special qube, but not as a powerful administrative service with root access and all. It is rather small, extremely limited and thus well protected. Generally, it is as it is, you don’t update it, it has no access to the network, no access to devices, no nothing, but for a shell for starting/stopping other qubes.
See, there is no center in this setting. We can hardly describe it as decentralized, but certainly there is no central point of possible failure here.
With Qubes OS, I found a renewed joy of using a computer. I am profoundly fascinated with it and, in hindsight, I think ~all operating systems should be like that, for the sake of reasonable security, that is!
Personal data
Personal data is, well, personal, right. Disregarding this tautology for the sake of nurturing one’s ignorance will be detrimental without exception. Why, personal data is what makes and enables our digital lives to be unique. Instead of using centralized cloud services, paying with monthly fees or worse, giving up our data to the provider who can mine it and sell further (we give them a blank license to do so), we can have our own clouds, either hosting them at home on an old dusty computer, or running it at a hosting provider, paying just for the hosting. One day, we will be able to host it in a decentralized storage, maybe not globally dispersed, but inside a private circle of trusted nodes of our own plethora of devices. NextCloud is one such project that enables us to have a private cloud. The basic setup is very straightforward, though a more customized installation will take some effort. NextCloud is completely free and open source. It has a full spectrum of features. We can store all our data there, making backups, versioning, even encrypting on the fly. Communication channels are fully developed. Instead of giving up our calendars to an almighty centralized provider, why not have a private calendar that can be shared to whomever we define? Better yet, I am now using a paper calendar mostly and feel quite liberated.

Phones vs. Computers
About communications … This is one of the most indicative trends in our digital lives. What is a telephone and what is a computer. At the surface, we can accept that the line is blurred and no longer worth contemplating about. Here, I suggest we take a rather drastic step back. Yes, back. To the point that the online world has spread like cancer to all aspects of our physical lives and having found a safe harbor in Qubes OS, the phones are nowhere near to being capable of such freedom. Why, the very phone is now smart. I do not accept this ridiculous fad. Everything is getting “smart” now, smart phone, smart cars … Some are even mentioning smart people. In my opinion, the smart part relates to the provider or manufacturer, not the device or user. It is how these devices are used in a smarter way, extracting value from the usage. Not so much to do about smart people. Borrowing the terminology from Richard Stallman, smart phones are about “useds”, not users (see https://stallman.org/glossary.html).

My computer is where I do my work, I consider it to be reasonably secure. I have an old computer-phone, which would be called smart phone, that I use when on the road, for things like setting up a hotspot or for getting a ride with Grab or MyCar or such horribly convenient transportation services; I consider this device to be completely insecure and do use it for sensitive activities like banking, not ever never, though from time to time I have some cryptos there, just like I carry some cash in my pockets occasionally. Disappointingly, I still need a telephone – for the silliest reasons imaginable, like for banking (they require me to have a phone and sometimes I need to verify payment transactions through an SMS). For this, I use a 10 EUR dumb phone, which I consider to be comparatively secure. It has no camera, no wifi capabilities, no GPS chip, nothing like that, so it can be abused in very limited ways. Why am I so sure about that? Simply because the cost of this phone is prohibitively low for any such contraptions.
Digital life, less centralized, more liberated
With some determination, I now mostly use open-source software and mostly without centralized services. The image is speaking for itself.
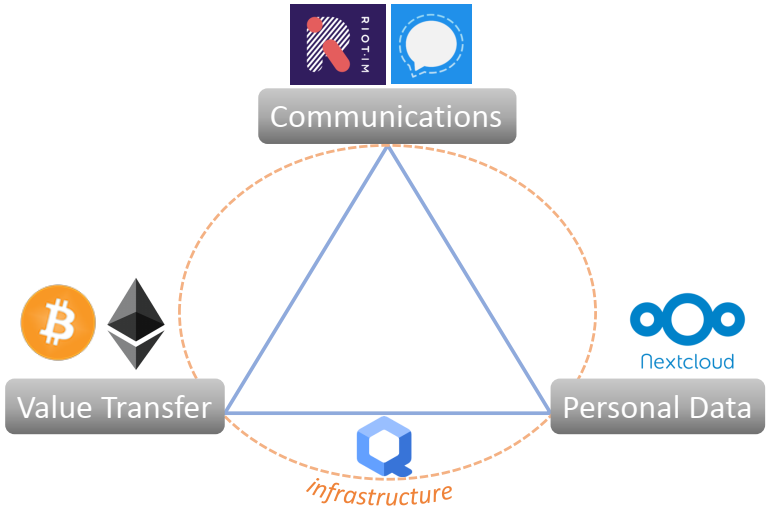
Instead of closed-source Whatsapp, which has integrated the protocol of Signal, we could just as well use a fully open-source Signal in the first place. Even better, there’s Riot, if we want to have messaging and video calls without requiring a phone number of email, which is useful when traveling and basically uncouples our communications from a relic like a phone number. Riot can also be used on your own chat server, having the full freedom of customizing the policies and metadata collection to suit our particular use case (or business case).
Can we realistically expect people to run their own nodes, manage their computers responsibly etc.?
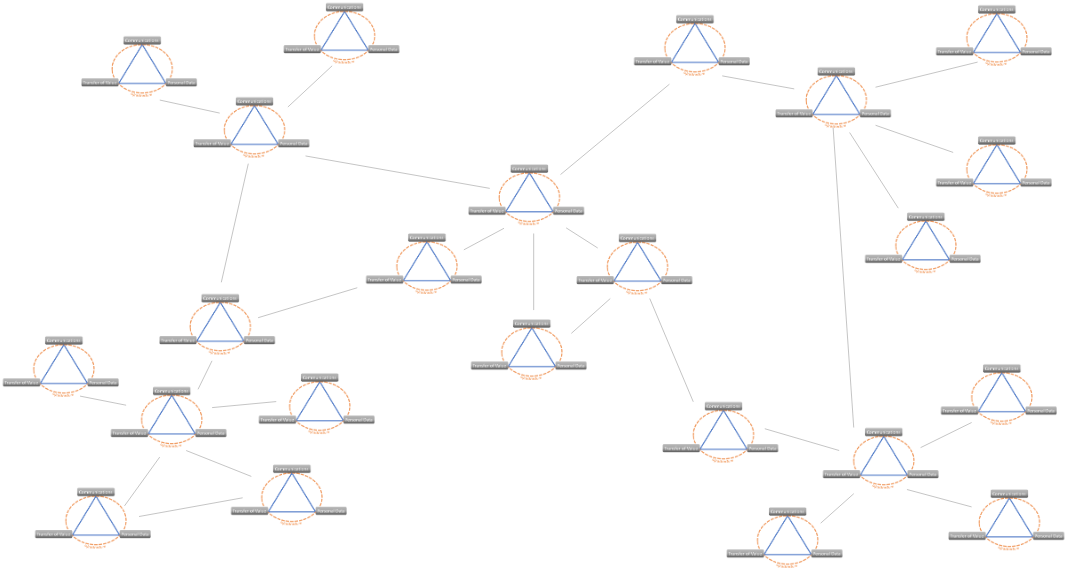
A little bit of help would come from forming clusters. Some instances of networks could be grouped, for example, I can run all this for my family, companies can do so for their employees and maybe a select number of partners, schools can very easily do so for their students. There is very little reason not to.
Nonetheless, not all data is equal. Some of it has no place to be in the public domain, while a significant portion of it could indeed be placed on a distributed file storage, like Swarm or IPFS, relying on a first-degree protection from encryption.
In Conclusion ...

Such a burden, is it worth it at all? It is a pain, but the best UX is not more important than fundamental utility. Using complex Qubes OS is as easy as it was using a regular PC two decades ago. I find it well worthwhile to sacrifice some convenience for a greater cause. User-friendliness has become a superficial excuse for complacency, which is a trend not everybody accepts anymore. Nonetheless, this is not a call to action, rather a brief report of a happy user who is giving community-lead free software a chance.
G